Hi there
How would you like to earn a 35% commission for each sale for life by
selling SEO services
Every website owner requires the use of search engine optimizaztion (SEO)
for their websites. Think about it, this is really hot
Simply register with us, generate your affiliate links and incorporate them
on your websites, thats it.
It takes only a few minutes to set up everything and the payouts are sent
by each end of the month
Click here to sign up with us, totally free:
https://www.creative-digital.co/join-our-affiliate-program/
See you inside
Gifford
SUPREMA SEGURANÇA
ALARMES, ANTENAS,INTERFONES, PORTOES ELETRONICOS, TELEFONIA, CERCA ELETRICA, CIRCUITO FECHADO DE TV,
Pesquisar este blog
segunda-feira, 15 de julho de 2024
domingo, 21 de abril de 2024
Collaboration request
Hi there
How would you like to earn a 35% commission for each sale for life by
selling SEO services
Every website owner requires the use of search engine optimizaztion (SEO)
for their websites. Think about it, this is really hot
Simply register with us, generate your affiliate links and incorporate them
on your websites, thats it.
It takes only a few minutes to set up everything and the payouts are sent
by each end of the month
Click here to sign up with us, totally free:
https://www.creative-digital.co/join-our-affiliate-program/
See you inside
Quintasha
How would you like to earn a 35% commission for each sale for life by
selling SEO services
Every website owner requires the use of search engine optimizaztion (SEO)
for their websites. Think about it, this is really hot
Simply register with us, generate your affiliate links and incorporate them
on your websites, thats it.
It takes only a few minutes to set up everything and the payouts are sent
by each end of the month
Click here to sign up with us, totally free:
https://www.creative-digital.co/join-our-affiliate-program/
See you inside
Quintasha
domingo, 28 de janeiro de 2024
Ettercap: Man In The Middle (MITM)
 "Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
"Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
Website: http://ettercap.sourceforge.net
- Hacking Tools Github
- Pentest Tools Bluekeep
- How To Make Hacking Tools
- Hack Tool Apk
- Hacker Hardware Tools
- Hacker Tools 2020
- Pentest Reporting Tools
- Hack Apps
- Hack Tools 2019
- Hacking Apps
- Hacking Tools For Games
- Hack Tools
- Hacker Tools For Ios
- Pentest Tools Review
- Hacker Hardware Tools
- Hacker Tools Linux
- Hack Tool Apk No Root
- Android Hack Tools Github
- Hacking Tools Pc
- Hacking Tools 2020
- Android Hack Tools Github
- Pentest Tools Online
- Hacking Tools Online
- Hacker Tools For Pc
- Hack Tools
- Pentest Tools Alternative
- Hack Tools For Windows
- Pentest Tools Windows
- How To Hack
- Hack Tools Github
- Hack Tools For Pc
- Hacker Tools
- Hacker Tools 2019
- Hacker Security Tools
- Physical Pentest Tools
- Physical Pentest Tools
- New Hack Tools
- Hack Tools Mac
- Hack Tools For Games
- Pentest Box Tools Download
- Hack Tools For Pc
- Hacking Tools For Pc
- Pentest Tools Website
- Pentest Tools Alternative
- Hacking Tools Github
- Black Hat Hacker Tools
- Hack Apps
- Hacker Tools 2020
- Growth Hacker Tools
- Hacking Tools Mac
- Hack Tools For Mac
- Termux Hacking Tools 2019
- Install Pentest Tools Ubuntu
- Hack Tools For Mac
- Nsa Hack Tools Download
- Hacker Tools
- Wifi Hacker Tools For Windows
- Pentest Tools List
- Black Hat Hacker Tools
- Hackers Toolbox
- Kik Hack Tools
- Hacker
- Top Pentest Tools
- Hackrf Tools
- Computer Hacker
- Hacking Tools Pc
- Hacking Tools Software
- Hacking Tools And Software
- Black Hat Hacker Tools
- Hacking Tools Software
- Pentest Tools Alternative
- Hak5 Tools
- Pentest Tools Find Subdomains
- Hacker Search Tools
- Hacker Tools 2019
- Hacks And Tools
- Pentest Tools For Mac
- Hacking Tools For Windows
$$$ Bug Bounty $$$
What is Bug Bounty ?
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organization's vulnerability management strategy.
Many software vendors and websites run bug bounty programs, paying out cash rewards to software security researchers and white hat hackers who report software vulnerabilities that have the potential to be exploited. Bug reports must document enough information for for the organization offering the bounty to be able to reproduce the vulnerability. Typically, payment amounts are commensurate with the size of the organization, the difficulty in hacking the system and how much impact on users a bug might have.
Mozilla paid out a $3,000 flat rate bounty for bugs that fit its criteria, while Facebook has given out as much as $20,000 for a single bug report. Google paid Chrome operating system bug reporters a combined $700,000 in 2012 and Microsoft paid UK researcher James Forshaw $100,000 for an attack vulnerability in Windows 8.1. In 2016, Apple announced rewards that max out at $200,000 for a flaw in the iOS secure boot firmware components and up to $50,000 for execution of arbitrary code with kernel privileges or unauthorized iCloud access.
While the use of ethical hackers to find bugs can be very effective, such programs can also be controversial. To limit potential risk, some organizations are offering closed bug bounty programs that require an invitation. Apple, for example, has limited bug bounty participation to few dozen researchers.
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organization's vulnerability management strategy.
Many software vendors and websites run bug bounty programs, paying out cash rewards to software security researchers and white hat hackers who report software vulnerabilities that have the potential to be exploited. Bug reports must document enough information for for the organization offering the bounty to be able to reproduce the vulnerability. Typically, payment amounts are commensurate with the size of the organization, the difficulty in hacking the system and how much impact on users a bug might have.
Mozilla paid out a $3,000 flat rate bounty for bugs that fit its criteria, while Facebook has given out as much as $20,000 for a single bug report. Google paid Chrome operating system bug reporters a combined $700,000 in 2012 and Microsoft paid UK researcher James Forshaw $100,000 for an attack vulnerability in Windows 8.1. In 2016, Apple announced rewards that max out at $200,000 for a flaw in the iOS secure boot firmware components and up to $50,000 for execution of arbitrary code with kernel privileges or unauthorized iCloud access.
While the use of ethical hackers to find bugs can be very effective, such programs can also be controversial. To limit potential risk, some organizations are offering closed bug bounty programs that require an invitation. Apple, for example, has limited bug bounty participation to few dozen researchers.
Related word
- Hacker Tools Free Download
- Hack Tools
- Hack Tools For Pc
- Pentest Reporting Tools
- Pentest Reporting Tools
- How To Hack
- Hacks And Tools
- Hacking Tools For Windows Free Download
- Hacker Tools For Ios
- Pentest Tools Alternative
- Free Pentest Tools For Windows
- New Hacker Tools
- Tools 4 Hack
- Hacker Tools Github
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Github
- Hacking Tools Hardware
- Pentest Tools Free
- Hacking Tools 2019
- Install Pentest Tools Ubuntu
- Best Hacking Tools 2019
- Hacker Hardware Tools
- Hacker Tools Online
- Hacking Tools Software
- Nsa Hack Tools
- Ethical Hacker Tools
- What Is Hacking Tools
- Hacker Tools Apk
- Bluetooth Hacking Tools Kali
- Computer Hacker
- Nsa Hack Tools
- Free Pentest Tools For Windows
- Hacking Tools 2020
- Hacking Tools For Windows
- Hacking Tools For Windows
- Hack Tools 2019
- Hacker Security Tools
- Pentest Reporting Tools
- Hacker Tool Kit
- Hacker Tools Github
- Hak5 Tools
- Pentest Tools Android
- Pentest Tools Bluekeep
- Pentest Tools Website
- Hack Website Online Tool
- Hacker Tools Free Download
- Free Pentest Tools For Windows
- Hacking Tools Windows
- Hacking Tools Online
- Pentest Tools Framework
- Usb Pentest Tools
- Github Hacking Tools
- Pentest Tools Open Source
- Hack Website Online Tool
- Hacker Tools List
- Best Pentesting Tools 2018
- Hackrf Tools
- Pentest Tools Url Fuzzer
- Hack Tools 2019
- Hacker Tools List
- How To Make Hacking Tools
- Pentest Tools Alternative
- Hacker Tools For Ios
- Hack Apps
- Physical Pentest Tools
- Hack Tools For Mac
- Hack Rom Tools
- Pentest Tools Android
- Pentest Automation Tools
- Ethical Hacker Tools
- Hacker Techniques Tools And Incident Handling
- Hack Tools
- Pentest Tools Windows
- What Is Hacking Tools
- Hacking Tools For Games
- Hack Tools Download
- Hack Rom Tools
- Hacking Tools For Pc
- Blackhat Hacker Tools
- Pentest Tools For Windows
- What Is Hacking Tools
- Pentest Tools Free
- Ethical Hacker Tools
- Best Hacking Tools 2019
- Pentest Box Tools Download
- Hack Tools Online
- Github Hacking Tools
- Hack Tool Apk
- Pentest Tools Url Fuzzer
- Pentest Tools For Android
- Hacking Tools
- Beginner Hacker Tools
- Hacker Tools List
- Pentest Tools For Android
- Hacking Tools 2019
- Black Hat Hacker Tools
sábado, 27 de janeiro de 2024
Hackerhubb.blogspot.com
Hackerhubb.blogspot.com
Read more
- Pentest Tools Open Source
- Hacker Tools Online
- Pentest Recon Tools
- Wifi Hacker Tools For Windows
- Hacking Tools Pc
- Pentest Tools Apk
- Hacking Tools
- Free Pentest Tools For Windows
- Pentest Tools Bluekeep
- Hacker Tools Apk Download
- Hacking Tools Online
- Hacking Apps
- Hacker Tools Apk
- Wifi Hacker Tools For Windows
- Hak5 Tools
- Hacking App
- Nsa Hack Tools
- Hacking Tools Software
- Pentest Tools Github
- Hacker Tools Github
- Pentest Tools List
- Pentest Tools Alternative
- Pentest Tools Linux
- Pentest Tools For Android
- Hacking Tools For Windows
- Game Hacking
- Hacker Tools Github
- Hacking Tools For Windows
- Hacking Tools Hardware
- Hack Tools 2019
- Pentest Tools Windows
- Hacker Search Tools
- Hack Tools Github
- Hacking Tools Hardware
- Hacking Tools For Windows
- What Are Hacking Tools
- Hacking Tools Mac
- Nsa Hack Tools
- Hack Tools Mac
- Pentest Tools Bluekeep
- Pentest Tools Windows
- Hacking Tools For Mac
- Hacker Tools For Ios
- Hacking Tools Name
- Pentest Tools Website
- Nsa Hack Tools
- Hacking Tools Free Download
- Tools For Hacker
- Hack Tools For Games
- What Is Hacking Tools
- Termux Hacking Tools 2019
- Hacking Apps
- Computer Hacker
- Hacking Tools Pc
- Pentest Tools Alternative
- Hacking Tools Software
- Hacker Search Tools
- New Hack Tools
- Hacker Tools Online
- Pentest Tools Nmap
- Bluetooth Hacking Tools Kali
- Hack Tools 2019
- Pentest Tools Find Subdomains
- Pentest Tools Windows
- Pentest Tools Linux
- Hack And Tools
- Hacking Tools Online
- Pentest Tools For Ubuntu
- Pentest Tools Url Fuzzer
- Hacker Tool Kit
- Hacker Tools List
- Blackhat Hacker Tools
- Hacker Tools Free
- Hacker Tools Free
- Hacking Tools And Software
- Hacking Tools 2019
- Pentest Recon Tools
- Hacker Tools For Mac
- Hacker Tools For Ios
- Pentest Tools Find Subdomains
- Hacker Tools List
- Underground Hacker Sites
- Pentest Tools For Android
- Hacking Tools For Mac
- Hack Tool Apk No Root
- Hacker Tools Free Download
- Hacking Tools
- Pentest Tools Find Subdomains
- Hacking App
- Hacking Tools Mac
- Pentest Tools Framework
- Pentest Tools Windows
- Nsa Hack Tools
- Pentest Tools Find Subdomains
- Hacks And Tools
- Hacking Tools Usb
- Pentest Box Tools Download
- Pentest Tools Linux
- Pentest Tools Alternative
- New Hack Tools
- Physical Pentest Tools
- Hack Tools Github
- Pentest Tools Online
- Hack Tools 2019
- Hacking App
- New Hacker Tools
- Pentest Tools Windows
- Hack Tools For Windows
- Best Hacking Tools 2020
- Hacker Security Tools
- Pentest Tools Tcp Port Scanner
- Underground Hacker Sites
- Hack Tool Apk
- Hacking Tools Pc
- Hacking App
- Hacker Security Tools
- Easy Hack Tools
- Hacker Tools Online
- Hack App
- Hacker Tools Apk Download
- Pentest Tools Free
- Pentest Tools Windows
- Best Pentesting Tools 2018
- Hacker Tool Kit
- Hacker Security Tools
- Hacker Tool Kit
- Hacker Tools For Mac
- Game Hacking
- How To Install Pentest Tools In Ubuntu
- Hackrf Tools
- Pentest Tools Framework
- Hacker Tools Github
- Physical Pentest Tools
- Pentest Tools Linux
- Hacker Tools 2020
- Hacking Tools Mac
- Hacking Tools Github
- Pentest Tools Subdomain
- Hacker Tools Hardware
- Ethical Hacker Tools
- Hack And Tools
- Android Hack Tools Github
- Pentest Tools For Android
- Underground Hacker Sites
- Usb Pentest Tools
- Physical Pentest Tools
- Hacking Tools 2019
- Pentest Tools Port Scanner
- Hackers Toolbox
- How To Make Hacking Tools
sexta-feira, 26 de janeiro de 2024
15 Important Run Commands Every Windows User Should Know
There are several ways to efficiently access the files, folders, and programs in Windows operating system. We can create shortcuts, pin programs to the taskbar, Start menu shortcuts etc. but we can't do it for all programs in many cases. However, the Windows Run Command box is one of the most efficient ways of accessing system programs, folders, and settings.
In this article, I am going to share 15 most important Run commands for Windows users. These commands can make it easier to manage a lot of tasks.
How to open Windows Run command box?
You need to press Win+R (Hold Windows button then Press R)
Important Run Commands Every Windows User Should Know
1. %temp%
This is the fastest way to clear the temporary files from your computer. It can save a lot of space which was being wasted by temporary files.
2. cmd
This command will open the windows DOS command prompt. Windows command prompt is very useful for performing many tasks which are not possible using graphical user interface.
3. MSConfig
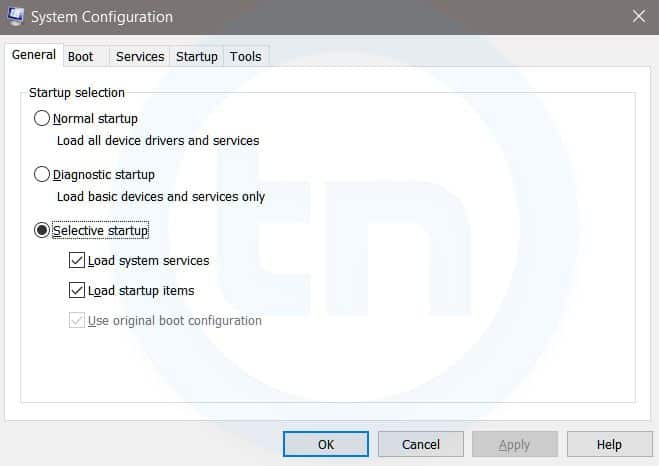
Windows System Configuration
This command will open Windows System Configuration where you can edit different things like the boot options, startup options, services, etc.
4. sysdm.cpl
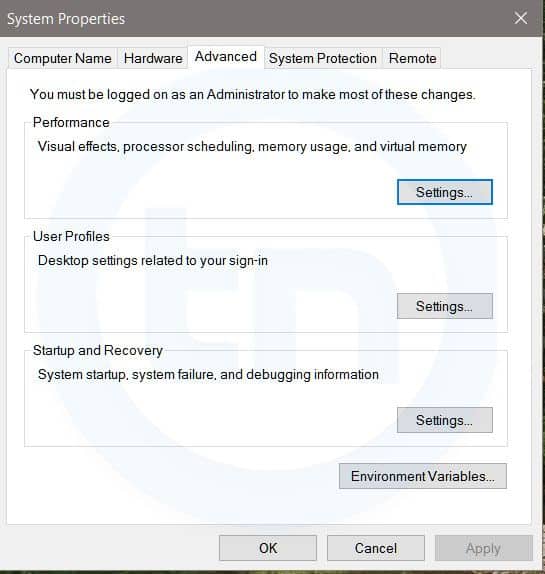
System Properties window
This command will open the System Properties window, Where you can change the system protection and performance related many settings
5. Powershell
Powershell is very similar the command prompt. Just type this command in the Run dialog box, and you will have your PowerShell opened without administrator privileges.
6. perfmon.msc
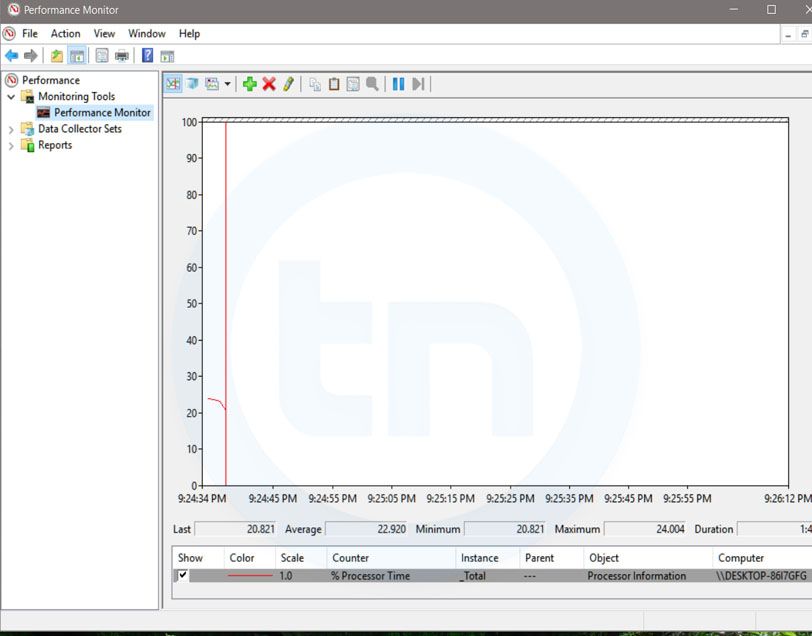
Windows System Performance monitor
This command can be used to monitor the performance of your computer. There are plenty of options for monitoring the system performance
7. regedit
Regedit Run command is used to open the Windows Registry. It is a hierarchical database that hosts all the configurations and settings of Windows operating system, it's users and the installed software.
8. \ (Backslash)
This is one of the lesser known Run commands. Just enter the backslash into the Run dialog box and it will open up the C drive. It is one of the quickest ways to access the C drive.
9. . (Dot)
This is yet another lesser known Run command. When executed, it opens the current user's home folder which hosts all the other local folders like the Downloads, Documents, Desktop, Pictures, etc.
10. .. (Double Dots)
When you execute these two dots in the Run dialog box, it will open up the Users folder which is located directly on the C drive
Also Read; Top 10 Great Gifts For Hackers
11. Control
This command will open the control panel. Control panel is used for managing all the system settings and programs
12. hdwwiz.cpl
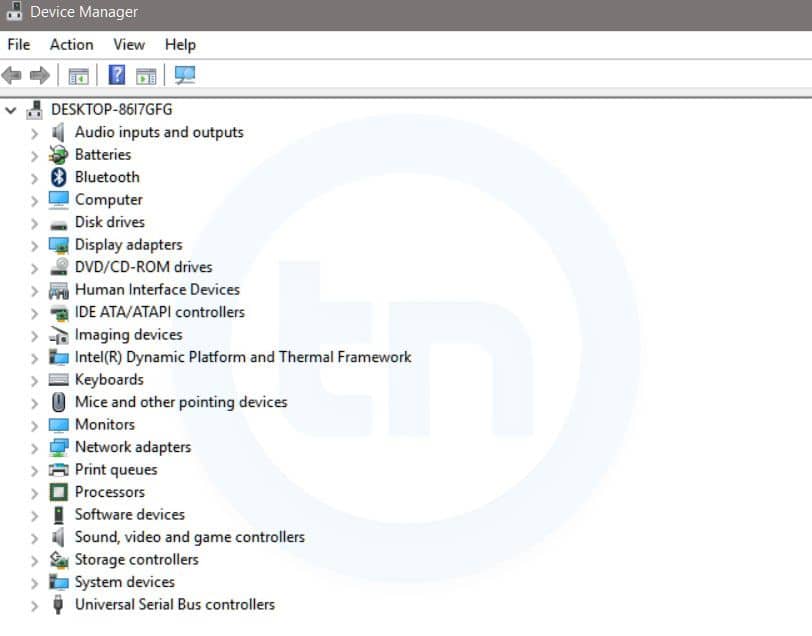
Windows Device Manager
This command is used to open the Device Manager in Windows. You can manage all the device connected internally or externally to your PC.
13. Notepad
The quickest way to open notepad in Windows. Just type this command in Run Box and hit enter.
14. osk
This command will open On-Screen Keyboard on your display monitor. You can easily touch and type or use your mouse for typing.
15. taskmgr
This command will open task manager where you can manage all the processes and programs running on Windows Operating system.
- Hacker Tools 2019
- Hacker Techniques Tools And Incident Handling
- Termux Hacking Tools 2019
- Pentest Tools Find Subdomains
- How To Install Pentest Tools In Ubuntu
- Blackhat Hacker Tools
- Termux Hacking Tools 2019
- Hacker Tools For Mac
- Hack Tools Pc
- Best Pentesting Tools 2018
- Hacker Tools Linux
- Hacking Tools For Beginners
- Hack Tools Download
- Hacker Tools Mac
- Hacker Tools For Ios
- Hacker Tools For Pc
- Hak5 Tools
- Free Pentest Tools For Windows
- New Hack Tools
- Pentest Recon Tools
- Kik Hack Tools
- Hacker Tools Linux
- Pentest Automation Tools
- Hacking Tools Download
- Hacking Tools 2019
- Nsa Hack Tools Download
- Github Hacking Tools
- Hacking Tools Windows 10
- How To Install Pentest Tools In Ubuntu
- Hacker Tools Apk Download
- Hacking Tools Github
- Hacker Tools Windows
- Pentest Tools For Android
- Hacker Tools
- Pentest Tools List
- Free Pentest Tools For Windows
- Hacking Tools And Software
- Pentest Tools For Mac
- New Hacker Tools
- Android Hack Tools Github
- Hacking Tools Github
- Hack Tools
- Hacking Tools Mac
- Hacker Techniques Tools And Incident Handling
- New Hack Tools
- Hacker Tools For Mac
- Tools For Hacker
- Hacker Tools For Mac
- Blackhat Hacker Tools
- Hack Rom Tools
- Hacking Tools For Windows Free Download
- Pentest Reporting Tools
- Hacker Tools Apk Download
- Pentest Tools List
- Usb Pentest Tools
- Tools 4 Hack
- Hacking Tools For Windows
- Hack Tools For Mac
- Ethical Hacker Tools
- Hacker Security Tools
- Hacker Tools For Ios
- Beginner Hacker Tools
- Hacking Tools Download
- How To Hack
Assinar:
Comentários (Atom)

